
The hidden risks of unmanaged visitor access
Hospitals and healthcare facilities are built on trust. Patients entrust medical professionals with their most sensitive information, relying on them to provide care while ensuring their privacy and security. But in an environment that sees a constant flow of visitors — family members, vendors, contractors, and even delivery personnel — how can healthcare organizations maintain airtight security while staying compliant with HIPAA regulations?
The reality is that visitor access is often overlooked in compliance strategies, leaving healthcare organizations vulnerable to privacy breaches, security threats, and regulatory penalties. A misplaced visitor log, an unauthorized person wandering through restricted areas, or an unattended laptop displaying patient records — all these seemingly small lapses can lead to major HIPAA violations.
For healthcare providers, ensuring compliance isn’t just about securing digital records; it’s about controlling physical access to sensitive areas and maintaining a detailed, auditable record of every visitor who enters the facility. This is where a modern visitor management system (VMS) becomes indispensable. By digitizing and automating visitor tracking, these systems help hospitals and clinics protect patient data, enforce access control, and demonstrate compliance in the event of an audit.
Understanding the role of visitor management in HIPAA compliance
The Health Insurance Portability and Accountability Act (HIPAA) sets strict guidelines for protecting patient health information (PHI). While much of the focus is placed on electronic record security, HIPAA also mandates that healthcare organizations prevent unauthorized access to physical spaces where patient data is stored or discussed. This means hospitals must have a strategy for controlling and monitoring visitors to ensure that sensitive areas — such as medical records offices, IT departments, and examination rooms — are only accessed by authorized individuals.
Traditionally, healthcare facilities relied on paper sign-in sheets to track visitor access. But this approach is both ineffective and non-compliant. Paper logs can be easily misplaced, falsified, or left unattended, exposing patient information to unauthorized eyes. Furthermore, handwritten records lack the detail and accuracy required for compliance audits, making it nearly impossible to prove exactly who accessed the facility and when.
A digital visitor management system replaces outdated processes with real-time monitoring, automated access control, and secure visitor data storage. It ensures that healthcare organizations have a reliable way to screen, document, and control visitor access — aligning with HIPAA’s strict privacy and security requirements.
How a visitor management system enhances healthcare security and compliance
A modern visitor management system transforms how healthcare facilities handle visitor access, replacing guesswork with structured, data-driven security protocols. From the moment a visitor arrives, the system can verify their identity, restrict access based on predefined criteria, and maintain an auditable record of their entry and exit.
One of the most critical functions of a visitor management system is automated identity verification and screening. Unlike paper logs that rely on self-reported information, a digital system ensures that every visitor provides verified credentials before being granted entry. Hospitals can require visitors to scan government-issued IDs, complete health screenings, and electronically sign non-disclosure agreements (NDAs) related to patient privacy. This reduces the risk of unauthorized individuals gaining access to sensitive areas while providing a layer of legal protection for the facility.
Beyond identity verification, visitor badges and access controls help enforce physical security. Instead of issuing generic, reusable badges, a digital VMS generates personalized, time-sensitive visitor passes that limit where an individual can go within the facility. For example, a vendor delivering supplies may only be permitted access to designated storage areas, while a patient’s family members are restricted to specific waiting rooms or patient floors. By customizing access permissions, healthcare organizations can prevent unnecessary exposure to PHI and mitigate security risks.
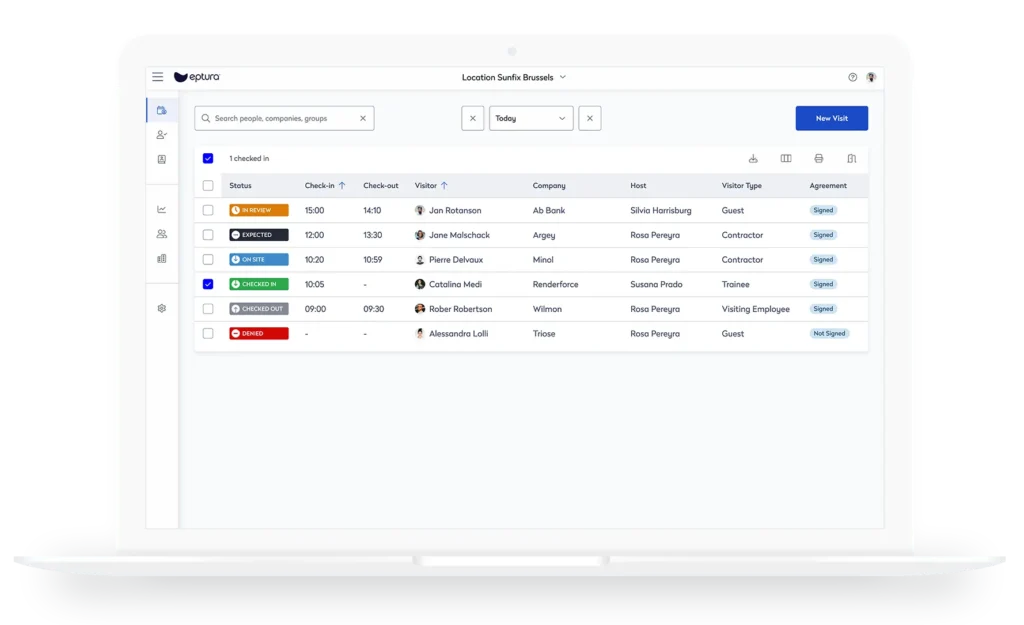
Hospitals must also be able to demonstrate compliance during audits, which is where detailed visitor tracking and reporting play a crucial role. A visitor management system automatically logs visitor data in a centralized, time-stamped database, allowing compliance officers to retrieve reports with the click of a button. If an incident occurs, facility managers can instantly review visitor logs to determine who was on-site, where they went, and how long they stayed. This level of detail is essential for ensuring HIPAA compliance and responding to regulatory inquiries with confidence.
Preventing privacy breaches and unauthorized access
Healthcare facilities are high-traffic environments, making it difficult to control who enters and what they see. Without strict visitor protocols, individuals may inadvertently gain access to restricted areas, overhear sensitive patient information, or even capture unauthorized photos. These seemingly minor incidents can lead to serious HIPAA violations, legal consequences, and reputational damage.
Consider the risk of tailgating — a scenario where an unauthorized person follows an approved visitor into a secure area without being properly screened. In a hospital setting, this could mean an unauthorized contractor accessing patient records, a reporter sneaking into a restricted ward, or a visitor wandering into an operating room. A visitor management system minimizes this risk by requiring individual identity verification and enforcing controlled access through badge scanning or mobile authentication.
Additionally, a digital VMS can integrate with security cameras, door access systems, and emergency response protocols, creating a comprehensive security network. If an unauthorized person attempts to enter a restricted area, the system can trigger alerts, notify security teams, and even initiate lockdown protocols. This proactive approach not only prevents privacy breaches but also enhances overall patient and staff safety.
A future-proof solution for modern healthcare facilities
As HIPAA regulations evolve and healthcare organizations face growing cybersecurity and privacy challenges, relying on outdated visitor tracking methods is no longer an option. The shift toward digital transformation isn’t just about compliance — it’s about creating a safer, more efficient, and more trustworthy healthcare environment.
A visitor management system does more than protect patient privacy; it optimizes workflow efficiency, reduces administrative burdens, and enhances the overall patient experience. By automating visitor check-ins, reducing wait times, and eliminating the need for manual record-keeping, hospitals can focus on delivering high-quality care rather than managing visitor logistics.
Additionally, as healthcare organizations expand their facilities and workforce, scalability becomes critical. Unlike traditional sign-in sheets, a digital visitor management system adapts to the evolving needs of the facility, accommodating everything from temporary health screening measures to enterprise-wide security integrations. Whether a hospital is managing one location or a nationwide network of clinics, a VMS provides the flexibility and control needed to enforce compliance at scale.
Elevating healthcare compliance with smart visitor management
In today’s healthcare landscape, ensuring HIPAA compliance requires a holistic approach to security — one that goes beyond data encryption and cybersecurity to address the physical access risks that many facilities overlook. A visitor management system bridges this gap, transforming the way hospitals control and document visitor access.
By automating identity verification, restricting access to sensitive areas, generating real-time visitor reports, and integrating with security protocols, a digital VMS provides an essential layer of protection for patient data, staff, and facilities. It ensures that healthcare organizations not only meet HIPAA standards but also create a safer, more efficient, and more transparent environment for everyone who walks through their doors.
As regulations tighten and patient expectations evolve, adopting a modern visitor management system isn’t just a compliance measure — it’s a strategic investment in the future of healthcare security.
Discover how a visitor management system like Eptura Visitor (Proxyclick) can help your healthcare facility streamline compliance, enhance security, and protect patient privacy.








