
Government agencies, with their complex networks and vast data stores, have always faced ongoing cybersecurity challenges that require sophisticated solutions. As they continue to embrace digital transformation at their facilities, security has never been more important. With more assets and processes online, agencies must implement new ways to keep them safe.
Key takeaways
- Cybersecurity is a shared responsibility across all departments in government agencies, not just the IT department
- The connection between physical and cybersecurity is crucial, requiring integrated security strategies
- Leveraging data from workplace systems can help establish baselines to detect potential security breaches
- When selecting a facility management solution provider, consider their track record, cybersecurity expertise, and data privacy policies
Part of the answer remains tried-and-true methods, including organizational vigilance and employee education. The digitization of workplace and facility management, though, means there are now more data sets agencies can leverage to strengthen overall security.
The growing importance of cybersecurity for government agencies
In 2024, the number of politically motivated cyberattacks against U.S. federal entities surged, with 117 government organizations reporting ransomware incidents, up from 95 in 2023, according to Statista.
At the municipal level, 60% of state and local governments reported experiencing a cyberattack in the past 12 months, and 45% of municipalities acknowledged service interruptions due to these incidents
The actual numbers are likely higher. The Statista report notes, “As with other sectors it’s important to acknowledge that it likely represents only a portion of the actual impact. Many ransomware attacks go unreported for reasons such as concerns about national security and the desire to avoid disrupting critical services.”
In terms of financial impact, the average cost of a data breach for a government entity reached $9.5 million in 2024.
Common misconceptions about cybersecurity
Improved safety starts with clearly defining cybersecurity.
One of the more common misconceptions is that cybersecurity is the exclusive responsibility of the IT department. While the IT department plays a critical role, they can’t do it all. Cybersecurity is a shared responsibility, and every department across the enterprise is involved. In fact, every employee has a role to play in protecting the company.
For example, employees need to be aware of the latest cybersecurity threats and how to protect themselves from them. They also need to be careful about what information they share online about themselves and the company.
Another common misunderstanding is that cybersecurity is a one-time investment.
Cybersecurity is an ongoing process because the landscape is constantly changing, so agencies need to constantly update security measures to stay ahead of the curve by implementing software patches, updating security policies, and training employees on the latest threats.
Understanding the connections between physical and cybersecurity
One of the largest misconceptions is that cybersecurity is only about protecting your network and data. While that’s an essential part of the process, it’s only one piece of the puzzle.
Cybersecurity also involves protecting:
- People
- Processes
- Physical assets
For example, a cybercriminal could gain access to your network through a phishing attack, then use that access to steal sensitive data, or even disrupt your operations. They could steal credentials online and then use them to gain physical access to your facilities. Or, working in reverse order, they would break into a facility for easier access to sensitive material through an onsite terminal.
For example, when a city’s water treatment facility is outfitted with sensors and control systems connected through the Industrial Internet of Things (IIoT), a cyberattack can be just as disruptive and dangerous as someone physically tampering with the equipment. Several U.S. municipalities have reported attempted breaches of water infrastructure systems, prompting federal alerts and emergency response coordination.
Or when a police department’s vehicle fleet is equipped with GPS and remote access systems, a hacker can compromise officer safety or operational integrity just as easily as a car thief once could with a crowbar. In a 2024 incident, a ransomware attack on a county sheriff’s office disabled dispatch systems and vehicle tracking for over 48 hours, delaying emergency response times.
These examples underscore the need for integrated security strategies that protect both digital and physical assets. For government agencies, this means aligning cybersecurity protocols with facility access controls, surveillance systems, and emergency preparedness plans to ensure continuity of public services.
How to strengthen cybersecurity: Standard best practices
With the rise of sophisticated cyberattacks, it is essential to take proactive measures to protect sensitive data and infrastructure, including:
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security to your organization’s systems and data. By requiring users to provide multiple forms of identification, such as a password, a security token, or a biometric identifier, MFA significantly reduces the risk of unauthorized access to sensitive information
- Educate employees: Educating your employees about common cyber threats, such as phishing emails and social engineering techniques, helps them identify and report potential security incidents. Conduct regular training sessions and awareness campaigns to ensure employees understand their role in maintaining the organization’s security
- Run security audits: Regularly conducting comprehensive security audits is a crucial step in identifying vulnerabilities and potential security risks within your organization. Audits help organizations assess various aspects of IT infrastructure. By identifying vulnerabilities early on, you can take the necessary steps to mitigate risks and prevent potential breaches
Together, these practices form a strong foundation for defending against evolving threats. By staying vigilant and continuously improving cybersecurity protocols, government agencies can better protect public data and maintain uninterrupted access to essential services.
How to strengthen physical security: Standard best practices
As threats to government facilities become more complex, strengthening physical security is just as critical as securing digital systems.
Agencies can take deliberate steps to safeguard buildings, assets, and personnel through proven strategies, including:
- Implement access control systems: Use mobile credentials, biometrics, and cloud-based platforms to control who enters your building. Integrate visitor management tools for real-time oversight and audit trails
- Monitor entrances and exits: Deploy smart surveillance systems with AI-powered analytics, motion detection, and facial recognition. Ensure coverage of all key access points and integration with alarms and access logs
- Manage visitor access: Digitize check-ins with QR codes, pre-registration, and automated badge printing. Use watchlists and alert systems to flag potential risks while maintaining compliance with privacy laws
- Run security audits: Perform scheduled reviews of systems and policies, including penetration testing and compliance checks. Use scenario-based drills to test readiness and identify gaps
These measures help ensure that public sector facilities remain secure, resilient, and prepared to respond to both everyday risks and high-impact incidents. When paired with strong cybersecurity protocols, physical security plays a vital role in protecting the continuity of government operations.
Why comprehensive security also leverages facility management data
As the lines blur between physical and cybersecurity, there are opportunities for facility managers to work with IT departments and third-party software providers to increase security.
Traditionally, organizations have set up three distinct, siloed technology architectures at a facility:
- Cybersecurity
- Physical security
- Facility management
Cybersecurity architecture can include workstations, firewalls, virtual private networks (VPNs), and other security appliances. Physical system architecture includes combinations of cameras, badge readers, door sensors, and fire detection and suppression systems.
A modern facility management solution includes a robust feature set, with systems for asset tracking, desk and room booking, visitor management, occupancy and utilization tracking based on sensors, space planning, and move management. Added to these data sets are ones from IoT assets and equipment as well as operational technology (OT), hardware and software that detects or causes changes by directly monitoring assets, processes and events.
By capturing and analyzing data from your facility system, you can establish baselines for specific activities. Strong deviations from those baselines may indicate a security breach that your team can quickly investigate.
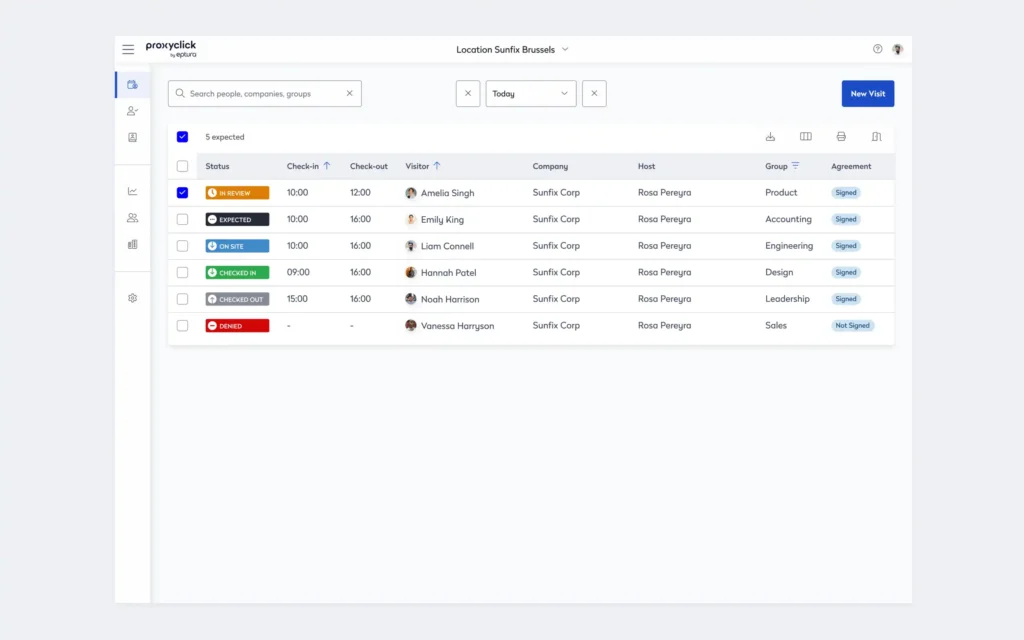
For example, you can create occupancy and utilization baselines using data from sensors, desk and room bookings, and visitor management systems. You might notice patterns like those in Eptura’s 2025 Workplace Index report, for example a midweek spike in activity, or you might find that your facilities behave differently from industry norms.
Digging deeper, you can track trends at specific controlled-access doors, especially those leading to server rooms or other sensitive areas.
A modern facility management system helps you establish baselines by providing answers to basic questions about your facilities, including:
- How often do employees access different spaces in each building?
- Is access more frequent in the morning, afternoon, or after hours?
- Are certain days busier than others or is occupancy generally steady?
- How often is access denied and what are the most common reasons?
Once you’ve established these baselines, you can monitor for anomalies. A sudden increase in access during off-hours could signal covert activity. A spike in access denials might mean someone is testing stolen credentials to find one that works.
How to select a facility management solution provider that can protect you and your data
When selecting a software vendor, it’s essential to conduct thorough research and consider several key factors.
First and foremost, evaluate the vendor’s track record in providing reliable and effective security solutions. Look for a vendor with a proven history of success in the cybersecurity industry and a strong reputation for delivering quality products and services.
Another crucial factor to consider is the vendor’s cybersecurity expertise. Assess their technical capabilities, certifications, and industry affiliations to ensure they possess the necessary knowledge and skills to address the specific security challenges large enterprises encounter. Look for vendors that employ experienced cybersecurity professionals and invest in continuous research and development to stay ahead of threats.
Data privacy policies and compliance with industry standards are deciding factors. Carefully review the vendor’s data handling practices, privacy policies, and security measures to ensure they align with your organization’s data protection requirements. Look for vendors that are transparent about their data usage and adhere to industry-recognized security standards.
The value of FedRAMP
For U.S. government agencies, the FedRAMP marketplace simplifies the process of finding solutions.
“You actually are building an information system for federal government use, and the government is authorizing that system for use for federal data,” explains James Masella, vice president of compliance advisory services at Coalfire, a provider of IT security assessments for many security standards and payments frameworks and programs, including FedRAMP support.
After passing a rigorous security audit, vendors are listed in the FedRAMP Marketplace, where federal agencies can easily find and procure cloud services. While agencies may still assess specific risks, FedRAMP streamlines the process by providing a standardized, reusable security framework.
In the end, a proactive approach to finding cybersecurity partners is essential for government agencies that need to protect assets, maintain trust, and ensure continuity in the face of evolving threats.
Connect, network, and learn at GSX with Eptura
Right now, security is top of mind for many, with experts coming together for Global Security Exchange (GSX) 2025, Sept. 29–Oct. 1.
The annual event includes experts from across the security industry and features opportunities to earn CPE credits, explore the latest technologies, and build strategies to stay resilient against today’s cyber and physical threats.
Eptura is excited for the opportunity to present at the event and share insights from our Workplace Index report and advice from our industry experts.
Securing the Smart Buildings of 2025: Bridging Gaps in an Era of Convergence
Time and date: 9:45–10:45 a.m. Wednesday, Oct. 1
Presenters: Richard Noel, director of security operations and infrastructure, Eptura, and Matt Fox, vice president of product management, Eptura
Key takeaways:
- Understanding the convergence of IT, OT, IoT, and physical security systems
- Strategies for securing smart buildings in complex hybrid environments
- Tools and technologies for enhancing security, including AI, analytics, and integrated platforms
- Bridging gaps between physical and digital security teams
As smart buildings and connected technologies reshape how you manage your spaces, the convergence of physical security with OT, IoT devices, and facility management platforms introduces new layers of complexity. While these innovations offer greater efficiency and insight, they also expose your organization to evolving cyber-physical threats that demand a more integrated and proactive approach to security.
The presentation will cover the most pressing challenges facing security professionals in 2025 and gain practical strategies for protecting your assets, people, and data. You’ll learn how to identify emerging risks, respond to disruptions in interconnected environments, and use data from your systems to improve decision-making and incident response.
Also make sure to visit Eptura at Booth 512 explore facility solutions built to support smarter, more efficient facility operations. The team will be available to explain product capabilities, discuss integration strategies, and answer questions about how Eptura fits into security programs.









